ClevGuard Support: Monitor Devices with Others' Permission.
Before We Start
Have you ever received a strange text message with a link, then clicking on it and nothing happens? Why>>
Does someone know your mobile service account password? Why>>
Is iCloud syncing enabled on your phone? Why>>
Have you noticed some problems with your mobile phone, such as poor performance, short battery life, or a sudden increase in data usage? Why>>
If you answered yes to any of these questions, then chances are high that someone is reading your private text messages from their phone.
Part 1: Can Someone Read My Text Messages from Their Phone
The answer is yes. Some people would read your text messages on their phone, but only if there is a good cause for that. For example, government agencies, employers, or your spouse may get access to the text messages on your phone.
Government agencies may enter your phone to read your text messages if they suspect of a crime, fraud, or if they believe you have some bad intention to harm others. They would do that to prevent all those things for the benefit of society.
Employers can track and read text messages of their employees to ensure they are not slacking at work. If they suspect that some of their workers are wasting time, they may check out their text messages to see whether they spend their time texting.
Finally, spouses can check on their partners if they suspect cheating. Reading their text messages may be a good indicator of whether someone cheats or not, so this is something that many spouses do.
Knowing that someone can read your text messages from their phone is something very important to keep in mind. This way, you will be one step ahead and can avoid being monitored by others. Now let`s see how can someone do it and what you can do about it.

Part 2: How Can Someone Read My Text Messages from Their Phone
1. Phishing Messages
Phishing messages are a sneaky and tricky way to get access to someone`s text messages. Phishing messages are deceptive messages that usually contain a link that leads towards a fake website. Once someone clicks on the link or provides some personal information, their information can get stolen. That is why you should avoid opening up and reading texts from people or institutions you don`t know or that you suspect are fake.
Here are some useful tips on how to protect yourself from phishing text messages:
Do not respond to suspicious texts. If you do not know where does the text comes from, just delete it.
Never click and follow links in text messages if they appear suspicious.
Never download attachments with strange names and file extensions.
Never give your personal, sensitive information on pop-up screens. Legit organizations never ask for such information through pop-ups.
Install and use a strong filter for preventing phishing attempts and suspicious texts from coming into your inbox.

2. SIM Swapping
Maybe you are clever with phone security and already use two-factor authentication. Perhaps you think you are doing everything to protect yourself, and you have good protection on your accounts. But that often is not enough as hackers can bypass all that and can still break into your phone through SIM swapping.
What is SIM swapping? you might be asking. Well, SIM swapping is a method performed by your mobile service carrier when your phone is lost, for example. They are then moving your number to a new SIM card so you could continue using their services.
However, people with bad intentions can call mobile service carriers and falsely pose as customers. If they steal your personal information, they can tell carriers your information to obtain access to your accounts.
Hackers are tricking the phone companies to perform a SIM swap and steal your phone information. When they get that, they can read all your text messages and other information that is on your phone.
So how to protect yourself from SIM swapping? Here are useful tips for that.
Limit the personal information you provide online.
Never share more than a few basic details, because the more you share the easier it gets for someone to hack your security questions for ID verification.
Do not post your full name, home address, and phone number anywhere online.
Do not use easy numbers or birthdates as PINs.
Use a quality authenticator app for two-factor authentication.
Create complex, long passwords for your online accounts to minimize the risk of someone hacking everything in case your SIM is stolen.

3. Unauthorized Access to iCloud or Google Account
Can Someone Read My Text Messages from Their Phone by gaining unauthorized access to iCloud or Google account? Again, yes, it is possible.
Matter of fact, when someone hacks Google or iCloud account, they can get easy access to all kinds of information. If you back up your phone on either of these accounts, your photos, messages, location, phonebook, call logs, saved passwords, apps, and everything else can be easily hacked.
Online hackers may not find your vacation photos that useful unless you are some kind of celebrity, but they can blackmail you if they find out you have something valuable to them. By hacking your Google account, your Gmail also gets hacked, and Gmail is where most people store their sensitive information.
Remember – if your Google account goes down, everything else that is linked to it also goes down.
Keeping yourself protected is a must, so here are some important things you can do:
Enable powerful 2-factor authentication. With this feature enabled, even if someone finds out your password, they cannot hack into your account without getting physical access to your smartphone.
Create and use long, strong passwords. This is a must yet many people still use very weak and easy-to-guess passwords.
Use fake answers as answers to your security questions. A lot of valuable information can be gained from your social media accounts, and hackers can easily break into someone’s account based on that. Therefore, lie to trick them in case they try to hack you.
Enable login notifications. This way you will always be informed about sign-ins from new locations or gadgets.

4. Spy Apps
Spy apps became very popular in recent years. They make it very easy for people to remotely access text messages, emails, online history, multimedia, phonebooks, GPS locations, and many other things. Anything a person would want to access on someone`s phone can be done easily with these apps.
So how spy apps work? You just install the app on the target phone and then you monitor everything remotely from on online account. Of course, different apps come with different features, but most of them operate similarly.
Some spy apps used for reading text messages on phones include FlexiSpy, mSpy, XNspy, and Cocospy. However, all these apps have negative sides too. One of the cons that all these apps have in common is that they require rooting or performing a jailbreak of the phone to use them.
Besides that, they can also harm the phone by draining its battery, slowing down apps, or making the phone perform worse. All of that will lead to suspicion, causing monitoring activity to fail because you would be detected if you use them.
So you want to use a quality, undetectable app right? Then forget the mentioned above and go for KidsGuard Pro. This is your ultimate monitoring app for whatever you need it for. Best of all – there is no need to root or jailbreak the smartphone.
With KidsGuard Pro, besides reading text messages, you can track and monitor over 30 other files. Pretty much everything that is recorded on the phone. If you are interested in what you can do with it, just check out the free demo.
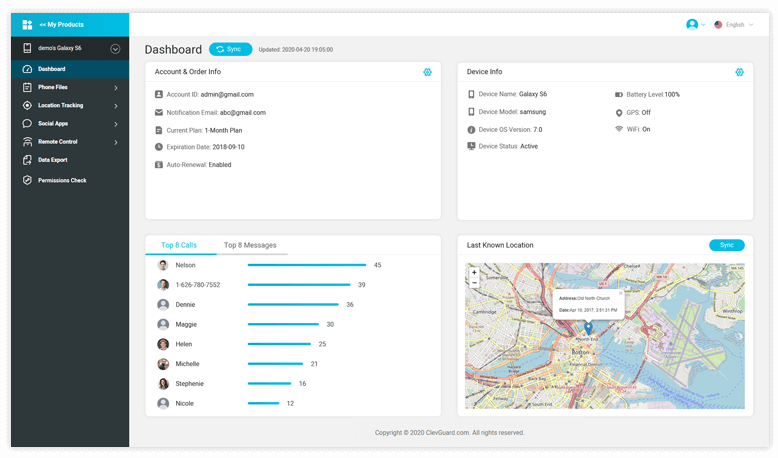
KidsGuard Pro certainly stands out from the other spy apps with its quality features and pros. You do not have to have special skills because it is a simple yet very powerful app. You can rest assured that is 100% safe and virus-free, it runs in stealth mode, and is very easy to install and use in just 5 minutes.






