ClevGuard Support: Monitor Devices with Others' Permission.
Can someone access my computer remotely without me knowing?
The answer is "Yes!".
This could happen when your devices are connected to the public internet or you are using your company and school's devices. If you have a slight suspicion of unauthorized access to your computer, then it’s quite essential to figure out if your computer is being monitored or not.
In this post, we will offer right methods to check if someone is remotely accessing your computer. Whether you are a Windows or Mac user, you will find the answers here.

- Part 1: Signs That Someone Might Be Accessing Your Computer Remotely
- Part 2: How to Know If Someone is Accessing My Computer Remotely
- Part 3: How to Stop Someone from Accessing Your Computer
- Spoiler: How to Check for Remote Access to Android
- Part 4: Is It Legal for Employer To Monitor Your Computer at Work?
- FAQ: about Remote Monitoring Computer
Signs That Someone Might Be Accessing Your Computer Remotely
Unusual Cursor Movement: One of the most apparent signs of remote access is seeing your cursor move independently, opening programs, or performing actions without your input.
Increased Network Activity: If your internet connection seems unusually slow, especially when you're not actively using it, it could indicate that data is being transferred remotely.
Unexpected Programs Launching: Programs or applications opening without your action can indicate that someone else is controlling your system.
Disabled Security Software: If your antivirus or firewall settings are suddenly disabled or altered without your knowledge, this could indicate that someone is trying to gain or has gained remote access.
Logins at Odd Hours: If your computer is waking up from sleep mode or logging in during odd hours when you're not using it, this could be a sign of unauthorized remote access.
How to Know If Someone is Accessing My Computer Remotely?
For non-tech-savvy computer users, it may be a tough job to tell if your computer is being monitored. It is actually not as difficult as you think. That provides the rationale for reading this article. We’ve come up with the most useful methods to determine whether someone is remotely accessing your computer. Just check them out to protect your computers.
Way 1. Check the List of Recently Accessed Files
Monitoring recently accessed files can help identify any unauthorized or suspicious access, aiding in data security. If you notice any unusual activities on your PC or Mac, you should immediately check the recently accessed files. It will clarify whether or not someone is accessing your computer.
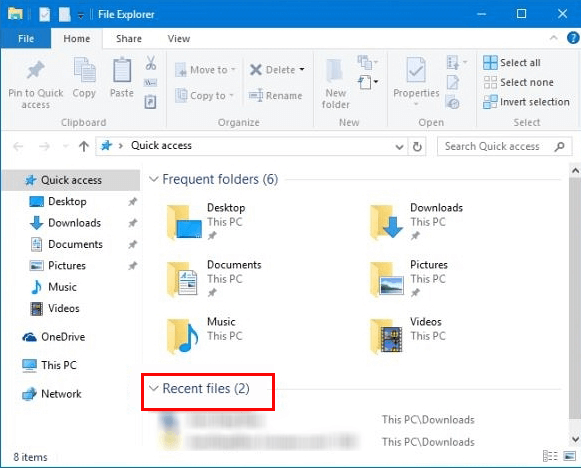
How to check the list of recently accessed files on Windows
Click on the taskbar shortcut.
Open the file explorer window, and open the document folder.
Select "quick access" from the left side of the file explorer window. Or you can also press Windows key + E. Then a list of recently accessed or viewed files will pop up. If any of the files in this list were not accessed by you, someone must be remotely monitoring your PC.
How to check the list of recently accessed files on Mac
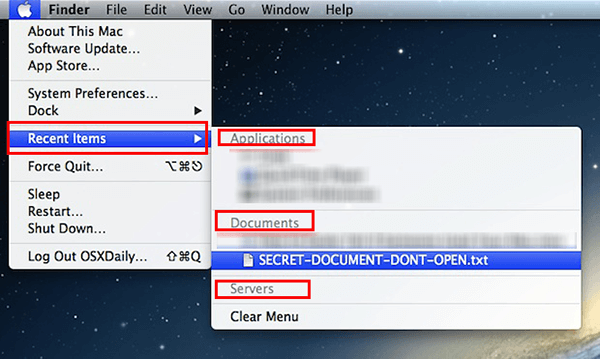
Check recent items:
Go to the menu bar on your Mac.
Then click on the Apple logo.
Move your cursor to "Recent Items", and a list of the last 10 accessed items will appear on the screen. They are divided into three categories: applications, documents, and servers. If you viewed all these items, relax; if not, it means someone is remotely viewing your computer.
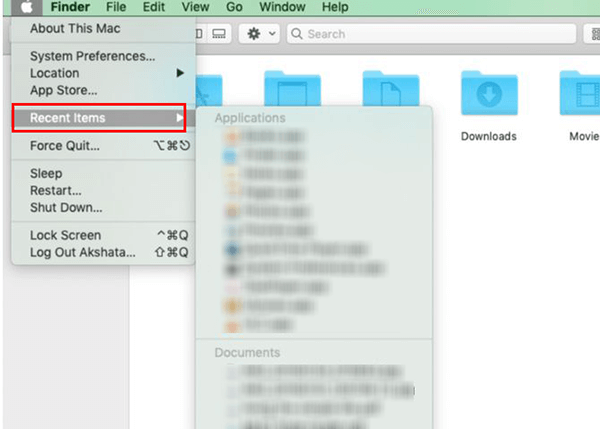
Check recent files:
Open a Finder window on your Mac.
Then click "Go" on the menu bar.
Move your cursor to "Recent Files", and then you'll see the 10 folders that were most recently accessed on your Mac. If any of the files in these 10 folders were not accessed by you, then you need to pay attention.
Way 2: Check Your Browser History on the Computer
Checking your browser history is also an effective way to tell if someone is remotely monitoring your computer. Regardless of what browsers you use, you can check the web history. Below are the detailed steps to check whether your computer is being monitored on some mainstream browsers.
How to check your browsing history on Google Chrome
Go to Google Chrome.
Click on the three dots on the upper right corner, and click "History".
Your entire search history will open. Now analyze carefully and see whether or not you have done all the searches. If there are unusual searches, someone might be remotely monitoring your PC.
How to check your browsing history on Mozilla Firefox
Open Mozilla Firefox on your computer.
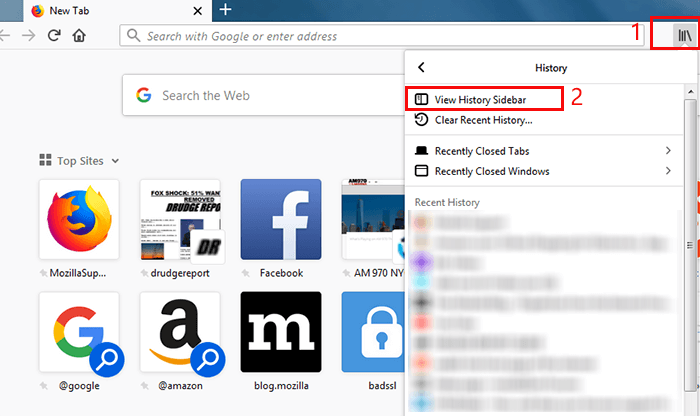
Click the icon that looks like a row of books and says "View history, saved bookmarks and more" on the menu bar.
Click on "History" and check the browsing activities on this browser.
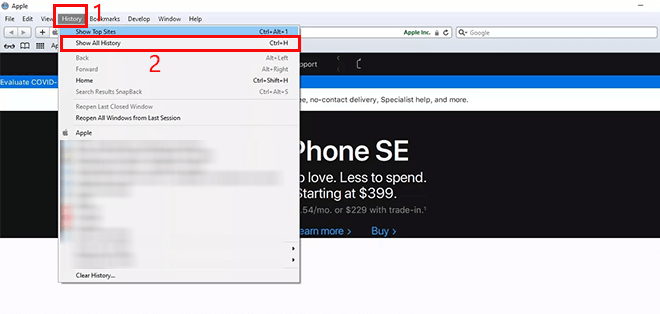
How to check your browsing history on Safari
Go to Safari on your Mac device.
Click on "History", and then "Show All History". Any search not made by you can be a sign of someone remotely viewing your device.

How to check your browsing history on Internet Explorer
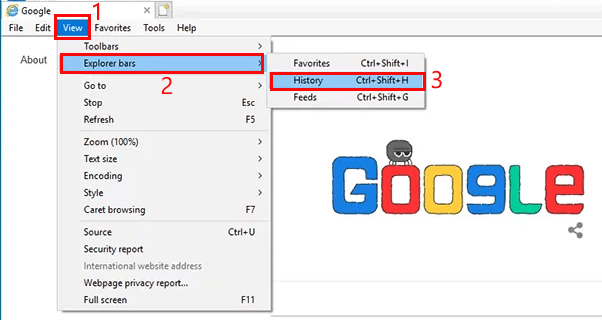
Launch Internet Explorer.
Then select the "Explorer bars" from the scroll-down menu.
Click on "History".
How to check your browsing history on Microsoft Edge
Launch Microsoft Edge on your computer.
Click the "Hub" icon at the menu bar.
Click on "History".

Way 3: Check Recently Modified Files
If someone gains unauthorized access to your computer, they may open, modify, or delete files. Checking recently modified files allows you to detect changes made by an unauthorized user. So you can check the history of the last accessed files on your computer to confirm if someone has used your PC remotely.
How to check recently modified files on Windows
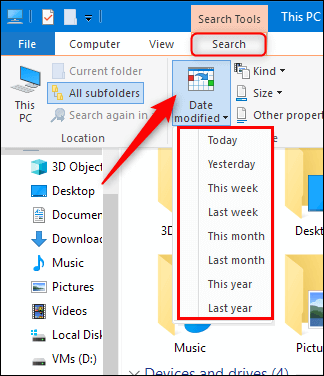
Open "File Explorer" on your computer.
To search the entire computer, select the "This PC" option.
Click the "Search" tab, and choose the "Date Modified" option, and then select a time range that you want to check. You can choose Today or go back to last month.
Steps to Check Recently Modified Files on Mac
Open the Finder on your Mac, choose File > Find.
Select "Kind" then choose "Other" in the pop-up window.
Choose "OK" button and then click "Kind" again. Then you will see System Files displayed in the window. Click System Files and choose "are included" option in the drop-down menu.
Click the "+" sign on the far right. Then change "Kind" to "Last modified date" and choose the time range you want to check, such as "Today".
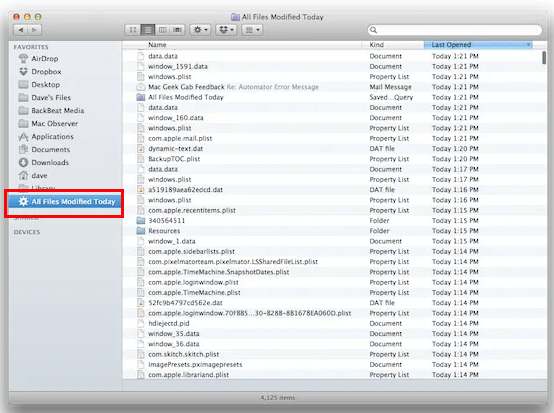
After that, you will see a list of files have been modified today on your Mac. Just confirm if you have modified them today.
Way 4: Check Your computer's Login Events
Checking the login activity of your computer is conducive to security breach prevention and suspicious activity detection. Follow the simple steps given below to figure out how to do it.
Steps to check login events on Windows computer
Go to the control panel and click on "System and Security" and "Administrative Tools".
Then click "Event Viewer". On the left side, an option "Security" will appear, click on it and wait for a window with all logon events to show. You will be able to detect any outsider by checking the administrative and standard logons and logoffs.

How to check login activities on Mac
Press Command + Space key to spotlight Search on your Mac.
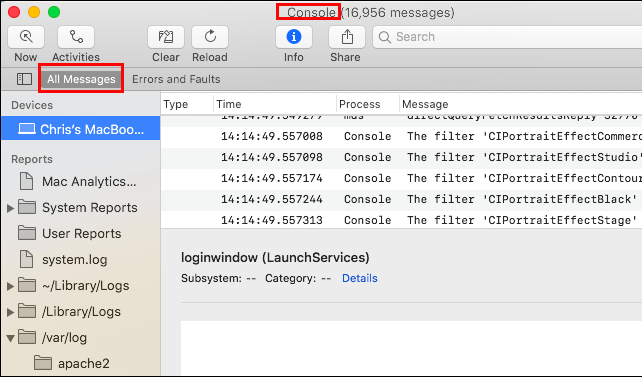
Type "Console" in the search box then press Enter.
In the next window, click "All Messages".
Then type "wake" to check all the login events and the time stamps.
Way 5: How to Detect Remote Access in Task Manager
The task manager can display all the running programs, whether they are hidden or not. That is to say, you can possibly notice some suspicious remote monitoring software running in the background. On a Windows computer, the app is called Task Manager, while on Mac, it is called Activity Monitor.
Below are the simple steps of using task management to check for remote access to your computer.
How to use Task Manager to detect remote access on Windows
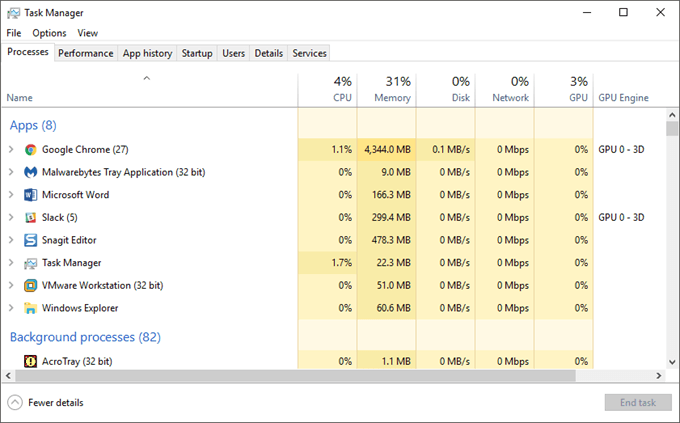
Open Task Manager from the taskbar menu and search for one of the options below.
Then you can check your list of running programs on your computer.
Any of the programs not executed by you is a clear identification of a remote viewer.
How to tell if your Mac computer is being monitored
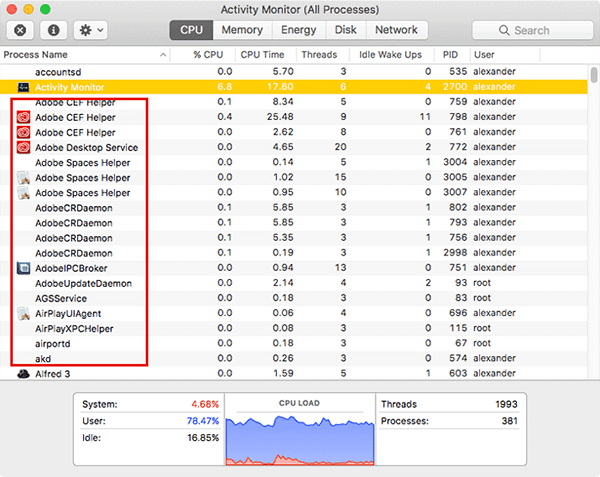
Open the Finder and click the "Applications" option in the window.
And open the "Utilities" folder.
Then double-click the "Activity Monitor" application. Then you can see all the open processes on your Macbook in the "Process Name" section.
Way 6: Check Your Firewall Settings
Checking the firewall settings is another approach to maintain the security of your computer and network.
If you find out a program has been granted access to bypass the firewall on your computer but you have no clue what it is, then follow the simple steps below to review your firewall settings and catch the spy.
How to check your firewall settings on Windows
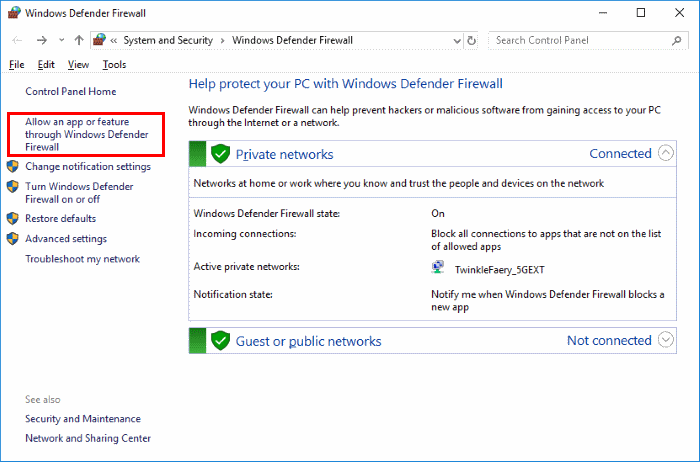
Go to your control panel and click on the "Windows Firewall" option.
If you notice that a program has moved past your Firewall without asking you, this could indicate that a programmer has empowered far off access.
If so, quickly eliminate any recent progressions to your firewall, restart your PC, and run the antivirus present on your PC, so no risk factors stay behind.
How to check your firewall settings on Mac
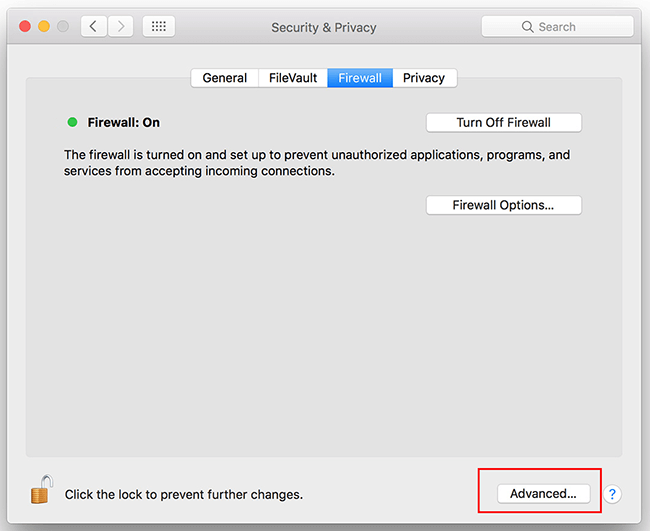
Choose "System Preferences" from the Apple menu on your Mac.
Then choose Security & Privacy and then the Firewall tab.
Click "Advanced" to check the firewall settings on your Mac.
Way 7: Scan your Computer for Viruses and Malware
Using anti-virus programs to scan your computer is not only an effective way of checking whether your computer is being remotely monitored but is also good for the overall health of your PC as well. It can flag any suspicious software on your computer, and you can get rid of them in no time by running the program.
How to scan viruses and malware on Your Computer
For Windows users:
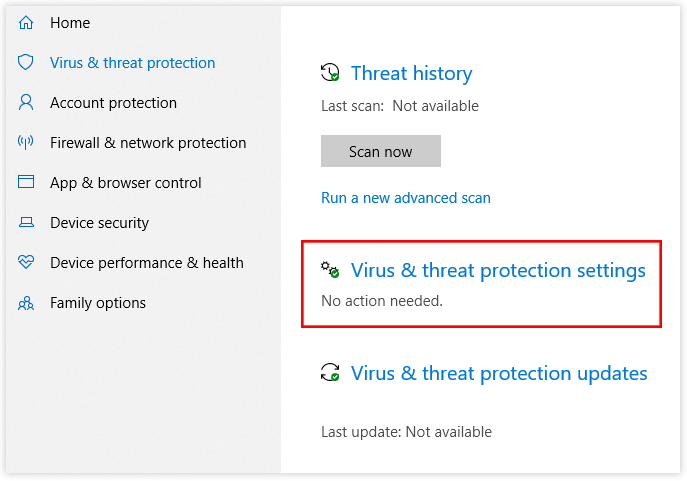
If you want to use the built-in tools for scanning, go to settings and choose "Update and Security” and then click on "Windows Security" and wait for scanning programs to appear. Run one of those programs and follow the on-screen prompts.
For Mac users:
It seems like Mac itself doesn’t have a built-in tool to scan for viruses and malware. So if you want to do that, you will need to use some third-party tools.
How to Stop Someone from Accessing Your Computer
How can you stop others from accessing your PC? You need to take action to protect your computer from these snoopers. There are three easy ways given below that can help you secure your computer.
Way 1: Disconnect Your Computer From the Internet
Connectivity makes everything possible. No internet means no one can remotely access your computer; if you doubt that someone is viewing your computer activity, disconnect your phone from the internet immediately. That’s not enough. Follow the steps below to completely keep your computer offline:
How to disconnect your computer from the internet
Turn off the router/WiFi.
Remove Ethernet cables.
Forget the network from WiFi settings.
Way 2: Update Your Password
If your password is old or easy to guess, it means it's super easy for anyone to get in. Do change your password immediately and make sure not to tell anyone.
Way 3: Lock Your Screen
If you are sure your new password is strong enough, the second step is to develop the habit of locking your screen every time you move away from the laptop.
It is so because when you lock your screen, the snooper will log out as well, and he will need a passcode to enter again. On most devices, the "lock screen" option appears next to "shutdown" in the main menu.
Way 4: Log Out of Everything Everywhere
Another method is to log out of everything everywhere. It will log you and the snoopers out. But the good part is that, you can log in again with the new password, while the snooper can't. Hence, it will be easier for you to keep a check on your computer's activity.
Spoiler: How to Check for Remote Access to Android
If you're concerned that someone might be spying on your computer, it's also worth considering the safety of your Android devices. Our ClevGuard is designed to help you detect and eliminate spyware on your Android smartphone or tablet, providing peace of mind that your personal data remains secure. In this section, we'll introduce how our software works and why it's an essential tool for protecting your privacy across all your devices.
If you want to know if your Android phone is being monitored or not, a third-party tool can be put to good use: ClevGuard.
Main features of ClevGuard:
Heuristic scanning to detect malicious and unsafe files
Check incoming and outgoing emails
Keep a close eye on hidden apps on your Android devices
Remove junk files and redundant data from cellphones
This software is safe to use and available on Google Play. So far, it has more than 100K downloads and received nearly 1,000 positive reviews. If you want to check if someone is remotely accessing your phone, try ClevGuard. I’m sure this reasonably priced anti-spy application will not fail you.
Is It Legal for Your Employer To Monitor Your Computer at Work?
Computer monitoring for employee is a common practice in many workplaces, especially in environments where sensitive data is handled or productivity is closely tracked. However, the legality of this monitoring raises questions about privacy and workers' rights.
In most countries, it is generally legal for employers to monitor computers and other work-related activities as long as the monitoring is conducted for legitimate business purposes. This includes monitoring email, internet usage, keystrokes, and even recording screen activity. The rationale behind this is that the employer owns the equipment and the network used for work, giving them the right to oversee how it is being used.
When Monitoring Might Be Unlawful
Monitoring can become unlawful if it is done excessively, without proper notification, or for purposes that are not related to business needs. For instance, monitoring private communications that are unrelated to work could violate privacy laws, especially if employees were not informed that such monitoring would occur.
FAQ about Remote Monitoring Computer
1. How do I know if my employer is monitoring my computer?
You can check for signs like the presence of monitoring software, unexpected processes running in the background, or restricted access to certain websites and applications. Reviewing company policies or directly asking your IT department can also provide clarity.
2. How do you tell if your screen is being monitored at work?
Your screen might be monitored if you notice a lag in your computer's performance, unexpected cursor movements, or if your company uses software known for screen monitoring. You can also check for remote desktop tools running in the background or look for notifications or warnings that indicate screen recording or sharing.
3. Can my employer see my PC activity?
Yes, your employer can see your PC activity if they have installed monitoring software or if you are using a company-owned device or network. This can include tracking websites visited, emails sent, keystrokes, and even real-time screen activity.
4. How does a company monitor your laptop?
Companies monitor laptops by installing software that tracks various activities such as internet usage, email correspondence, keystrokes, and screen activity. This software can also send regular reports to the employer. Additionally, companies may monitor through VPNs or by accessing log files on company servers.
5. Can my company track my laptop activity without VPN?
Yes, your company can track your laptop activity without a VPN by using monitoring software installed directly on the device. This software can monitor your activity even when you're not connected to the company's network. Other methods include tracking through specific applications or logging into company accounts.
Conclusion
There are various ways to tell if someone is remotely accessing your computer, and we've discussed some of the easy ones for you to detect whether your computer is being monitored or not. We hope it helps. Or you can tell us what you think in the "Comment" section below!







