ClevGuard Support: Monitor Devices with Others' Permission.
In today's digital age, computers play a crucial role in every workspace. Whether it's performing job tasks directly on a computer system or accessing it remotely, employees rely heavily on computers to get their work done efficiently.
However, with the vast amount of sensitive and confidential information stored and shared over interconnected computers, it has become imperative for businesses to implement computer monitoring systems. Therefore, what is computer monitoring?
Table of Contents
1. What Is Computer Monitoring?
3. How Does Computer Monitoring Work?
4. MoniVisor: Windows-based Computer Monitoring Software
5. Best Practices for Computer Surveillance
- Clearly Defined Policies
- Transparent Communication
- Selective and Targeted Monitoring
- Regular Audits and Reviews
What Is Computer Monitoring?
Computer monitoring, a form of electronic monitoring, refers to the processes and systems used to monitor and record user activity on a PC or computer network. It enables employers to keep track of employees' productivity, adherence to company policies, and overall conduct in the workplace. Computer monitoring is equally applicable to both in-office and remote work teams.
Types of Laptop Monitoring
Laptop monitoring encompasses various methods and tools to observe and track the activities and usage of laptops. Here are some common types of laptop monitoring:
Employee Monitoring
One aspect of computer monitoring is employee monitoring, which involves tracking various aspects of employees' computer usage. This can include monitoring their login details, keystrokes, visited websites, file transfers, time spent on different tasks, internet and application usage, and all internal and external communications via the company network.
Employee activity logs and time data are usually stored securely on servers as part of compliance programs, and analytics can be run on this data to identify patterns in employee behavior and improve productivity.
Network Monitoring
Another important aspect of computer monitoring is network monitoring, which involves tracking the performance and security of a computer network.
Network monitoring tools allow businesses to monitor network traffic, detect and troubleshoot network issues, and ensure the smooth functioning of the network infrastructure. This is particularly important for businesses that rely heavily on their network for daily operations.
Security Monitoring
In the realm of cybersecurity, security monitoring stands as a vital element of data security, vigilantly overseeing computer systems to detect insider threats, potential security breaches, unauthorized access, malware, and other that could compromise the integrity of the system.
Security monitoring tools can help businesses detect and respond to security incidents promptly, thus protecting sensitive data and preventing potential damage.
How Does Computer Monitoring Work?
What is computer monitoring? It encompasses the deployment of various tools and technologies for activity monitoring, allowing for the observation and documentation of computer, network, and user activities. Computer monitoring is characterized by specific components and methodologies:
Software Installation: Typically, computer monitoring entails the deployment of remote monitoring software on the designated computer or network to facilitate oversight.
Data Collection: Once the monitoring software is installed, it initiates the process of data collection regarding the activities occurring on the computer.
Data Storage: The collected data is usually stored locally on the monitored computer or transmitted to a central server for storage and analysis.
Remote Access: Many monitoring solutions allow authorized individuals or administrators to remotely access the collected data.
Reporting and Analysis: The collected data is often used to generate reports and perform analysis.
Legal and Ethical Considerations: It's important to note that computer monitoring must be conducted in compliance with legal and ethical guidelines.
Privacy Protection: Organizations conducting computer monitoring should implement measures to protect the privacy and confidentiality of the collected data.
MoniVisor: Windows-based Computer Monitoring Software
With a plethora of PC monitoring programs available, making a decision can be daunting. No worries, we recommend MoniVisor. This Windows-based pc monitoring software is tailored to offer comprehensive monitoring capabilities for businesses.
MoniVisor provides a suite of features that enable employers to effectively monitor and track employee computer activity. Here are primary features that MoniVisor offers:
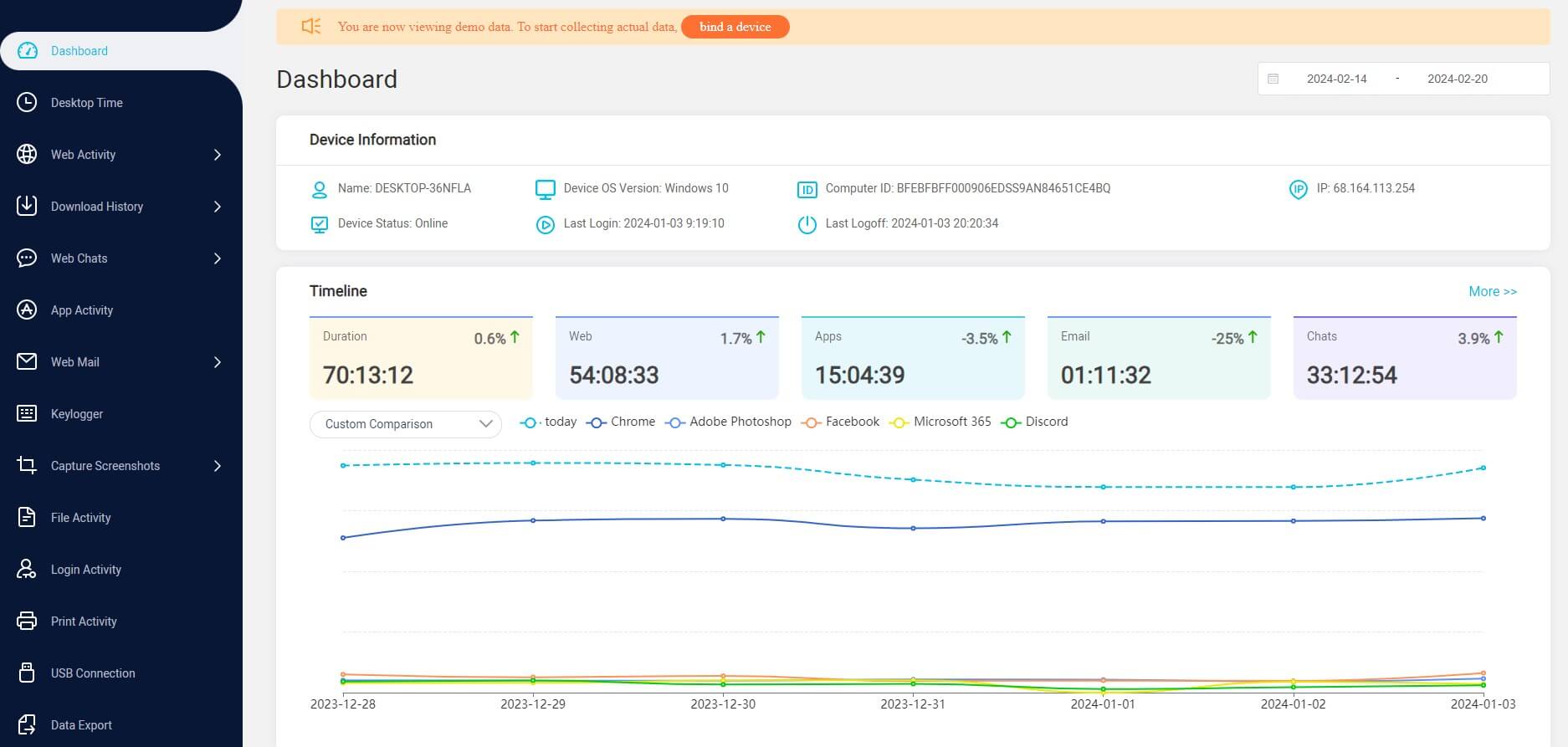
Desktop Time: Provide details of how the user interacts with the monitored device, inclduing the overall usage trend.
Keystroke Logging: Log the keystrokes made on a computer's keyboard and record in which software these keystrokes are typed.
Application Usage Tracking: Monitor and record the usage patterns of software applications on the target computer.
Live Screen: MoniVisor periodically captures screenshots and records screen activity to provide visual evidence of employee work.
Data Export: All the monitored data can be quickly exported to a local folder when you need to see it offline.
Best Practices for Computer Surveillance
Implementing computer monitoring systems requires careful consideration and adherence to best practices to ensure a balance between monitoring and respecting employees' privacy. Here are some best practices to follow:

Clearly Defined Policies
Before implementing computer monitoring, it is crucial to establish clear and well-defined policies that outline the purpose, scope, and limitations of monitoring. This helps set expectations for employees and ensures transparency in the monitoring process.
Transparent Communication
Open and transparent communication is key to successful computer monitoring. Employers should inform employees about the monitoring policy, including the types of data that will be collected, how it will be used, and how privacy will be protected. Clear communication helps build trust and reduces concerns about privacy invasion.
Selective and Targeted Monitoring
Before implementing computer monitoring, it is crucial to establish clear and well-defined policies that outline the purpose, scope, and limitations of monitoring. This helps set expectations for employees and ensures transparency in the monitoring process.
Regular Audits and Reviews
Regular audits and reviews of the monitoring system are essential to ensure its effectiveness and compliance with policies and regulations. Employers should periodically assess the data collected, review monitoring practices, and make necessary adjustments to improve the system's efficiency and protect employee privacy.
Benefits of Computer Monitoring
Implementing desktop monitoring systems can bring several benefits to businesses. Here are some key advantages:
Increased Productivity
By employing this method, you can identify and address productivity issues in real-time. By monitoring employees' computer usage, employers can identify time-wasting activities, address distractions, and provide guidance to improve productivity. This leads to better time management, reduced inefficiencies, and increased overall productivity.
Enhanced Security
Computer monitoring plays a crucial role in ensuring the security of company data and systems. By monitoring computer activity, employers can detect and prevent security breaches, unauthorized access, and other potential threats. This helps protect sensitive information and maintain a secure work environment.
Compliance with Policies
Desktop monitoring helps businesses comply with internal policies, industry regulations, and legal requirements. By monitoring computer activity, employers can ensure that employees adhere to company policies, such as acceptable use policies, data protection guidelines, and industry-specific regulations. Compliance with such policies reduces the risk of legal and regulatory issues.
Troubleshooting and Maintenance
Desktop monitoring provides valuable insights for troubleshooting and maintenance purposes. By monitoring computer performance and usage patterns, employers can identify and address hardware or software issues promptly. This reduces downtime, improves system reliability, and enhances overall operational efficiency.
To Sum Up
In conclusion, computer monitoring is a crucial strategy for businesses aiming to optimize their workforce, secure their assets, and foster a productive and secure work environment.
By utilizing desktop monitoring software like MoniVisor, companies can effectively monitor and manage employee computer activity, leading to enhanced productivity, robust security, and adherence to policies and regulations.






