ClevGuard Support: Monitor Devices with Others' Permission.
In today's digital landscape, data security is of paramount importance for organizations. Facing the escalating threats of cyberattacks and the risk of security breaches, it is crucial to implement robust measures to safeguard sensitive information and maintain data security.
One such measure is file integrity monitoring (FIM), a security mechanism that scrutinizes critical system files to detect unauthorized modifications and prevent cyberattacks. This article will explore the concept of FIM, underscore its significance, and discuss various methods to ensure file integrity.
What Is File Integrity?
File integrity refers to the state of a file or data being complete, unaltered, and trustworthy. It ensures that the content and structure of a file remain intact and have not been tampered with or modified without authorization.

Maintaining file integrity is crucial for data security and compliance purposes, as any unauthorized changes to files can lead to data breaches, loss of sensitive information, and compromised systems.
What Is File Integrity Monitoring?
File Integrity Monitoring (FIM) is a widely used security control mechanism in IT organizations. It involves examining the integrity of sensitive files, registry keys, and folders within the host operating system to check whether files have been altered or compromised.
FIM tracks logs and compares the current version of files to a known baseline, enabling organizations to monitor file integrity and detect unauthorized modifications.
File integrity monitoring tools automatically track and alert IT administrators to any unauthorized changes across critical files. These tools provide a comprehensive picture of all the activities that occur within an organization's network, facilitating real-time monitoring and generating out-of-the-box reports.
By using FIM tools, organizations can track changes made to critical files and folders, detect inappropriate access, and prevent security mishaps.
Why Verify File Integrity?
If you are pondering whether to implement file integrity monitoring in your enterprises or organizations, here are some persuasive perspectives you can take into account:
A. Detecting Unauthorized Changes:One of the primary reasons to verify file integrity is to detect unauthorized changes that cybercriminals may inflict on critical systems to compromise valuable and sensitive business data. By continuously monitoring system files for integrity, organizations can identify unwanted intrusions and prevent illicit activities that could disrupt their operations.
FIM solutions allow organizations to gain valuable insights into cyberthreats and the files targeted by threat actors, enabling them to take proactive measures to safeguard their data.

B. Ensuring Data Integrity: Data integrity is vital for organizations to maintain the accuracy, consistency, and reliability of their data. By verifying file integrity, organizations can ensure that their data remains unaltered and trustworthy.
Unauthorized changes to files can lead to data corruption or loss, compromising the integrity of the organization's data. File integrity monitoring helps organizations identify any changes made to critical files and take appropriate actions to restore data integrity.
C. Compliance with Security Standards: Compliance with security standards and regulations is a top priority for organizations across industries. File integrity monitoring plays a crucial role in meeting compliance requirements.
Organizations are often mandated by regulatory frameworks such as PCI DSS and HIPAA to incorporate file integrity monitoring into their comprehensive security measures. These standards ensure that entities handling sensitive information maintain a robust defense against potential breaches.
By verifying file integrity, organizations can demonstrate their commitment to data security and ensure compliance with industry regulations.

How to Check File Integrity
There are various methods to check file integrity, ranging from manual checks to system-specific tools. Let's explore some of the commonly used methods.
MoniVisor: File activity monitoring software
One popular file changes monitoring tool is MoniVisor. MoniVisor offers a comprehensive solution for monitoring computer activities, one of which is file monitoring capability. It enables organizations to track changes in sensitive files, folders, and other changes.
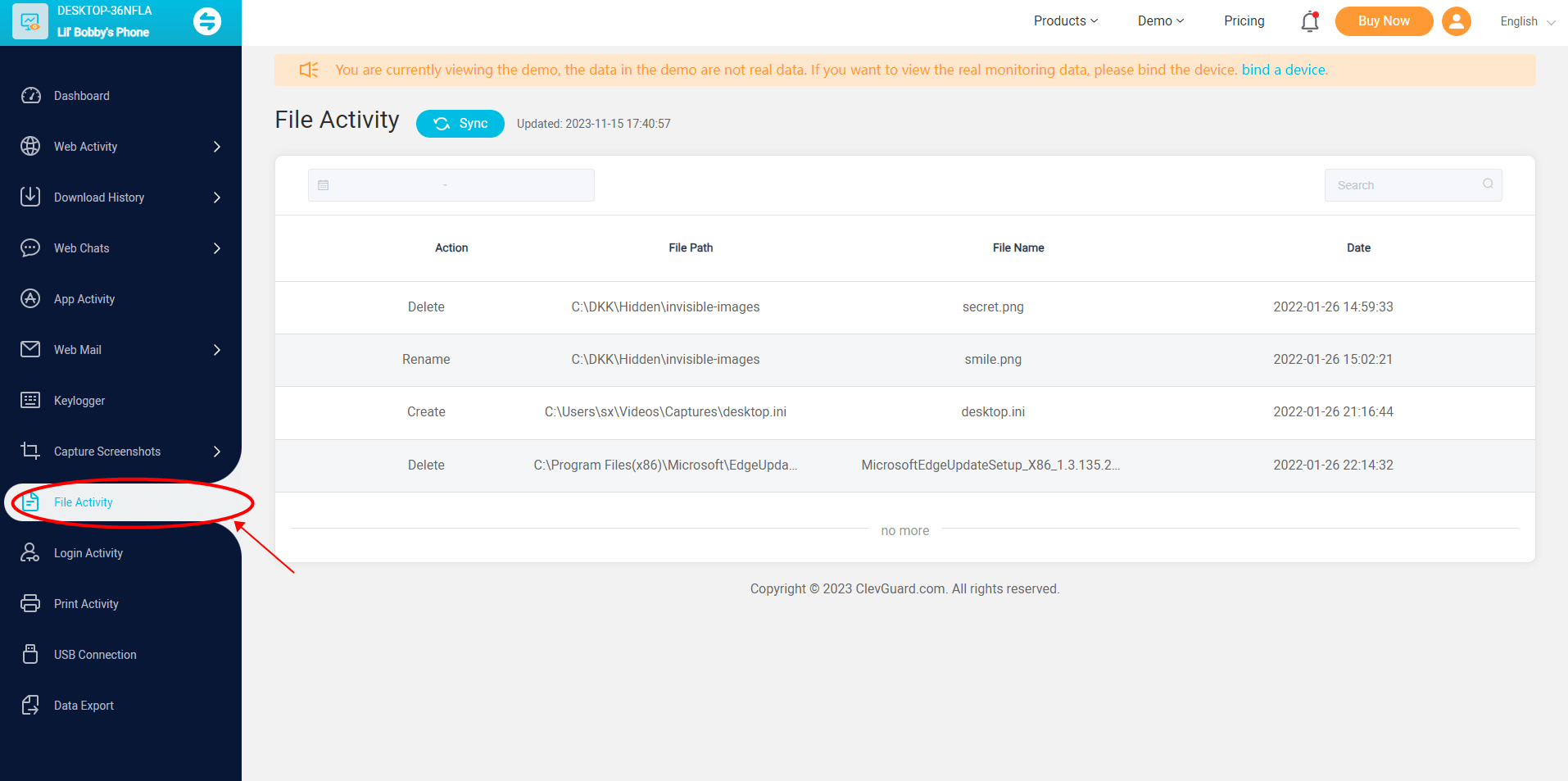
However, MoniVisor is not a professional FIM software program, and thus IT administrators cannot gain insights into the number of corrupted files, and are not able to restore the modified files, and prevent future illicit file access.
Related Post: Best File Activity Monitoring Tools in 2024
Manual file integrity checks
Manual file integrity checks involve comparing the current state of files to a known baseline or checksum. This involves calculating a cryptographic hash of the file and comparing it to the hash of the original file.
If the hashes match, the file has not been tampered with. However, manual file integrity checks can be time-consuming and impractical for large organizations with a vast number of files to monitor.
System-specific methods
Different operating systems provide system-specific tools and commands to check file integrity. Here are a few examples:
Windows: PowerShell Commands for file integrity
Windows operating systems, known for their robustness, include built-in utilities like the System File Checker (SFC) for file integrity checks. This command-line tool, integral to Windows, scans and verifies the integrity of system files,comparing them against a cached version stored in a compressed folder. Should the SFC detect any corrupted or altered files, it promptly replaces them with the correct cached copy, ensuring the stability of the Windows environment.
Within the Windows ecosystem, PowerShell stands out as a powerful scripting language offering commands such as the Get-FileHash cmdlet for file integrity checks. This cmdlet computes the hash value of a file, enabling users to compare it against a known baseline to confirm the file's integrity.
How to ensure file integrity on Mac
On macOS, the Terminal serves as a gateway to various commands for file integrity verification. Users can utilize the shasum command to calculate a file's SHA checksum, or the md5 command for generating and confirming an MD5 checksum, both of which are pivotal for maintaining the integrity of files on macOS.
Final Words
File integrity monitoring is a vital component of data security and compliance for organizations, safeguarding critical assets against unauthorized alterations. If all you need is a fundamental file activity monitoring tool, the MoniVisor proves to be a reliable program for Windows users.






